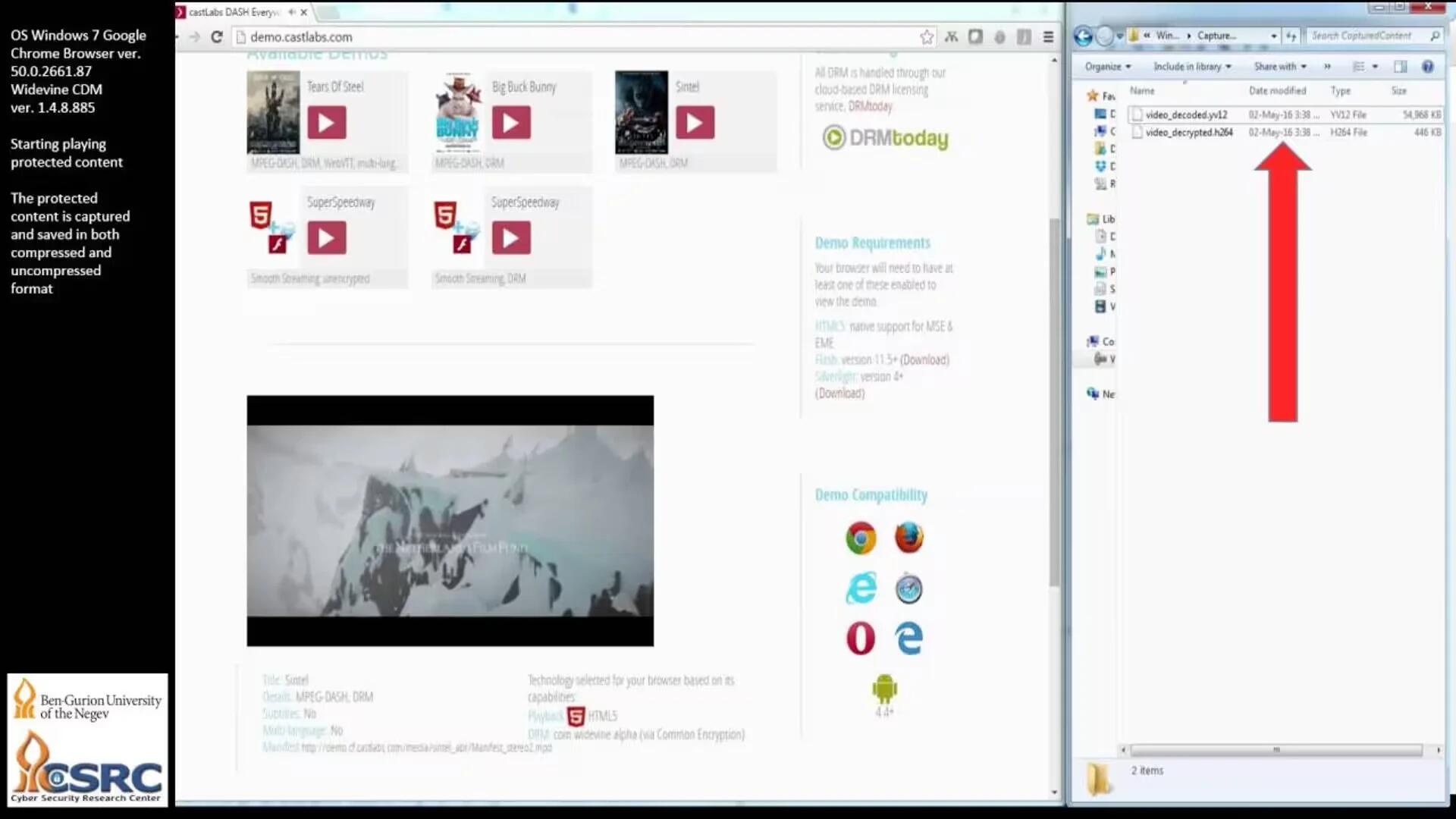
A recently discovered security flaw in Google Chrome allows users to capture any streaming video as it is passed to the browser’s media player. By exploiting this flaw, anyone can start copying Netflix videos with the right software.
This new flaw was found in Google’s Widevine digital rights management. The security researchers who found the flaw has not revealed how the technique works. However, they describe it as relatively simple. Also, it seems like the flaw exists since Google implemented Widevine in Chrome.
When you want to watch a DRM protected video from streaming services like Netflix, the following steps happen. First the Content Decryption Module (CDM) in your browser sends a license request to the provider through the Encrypted Media Extensions (EME) interface and receives a license in return. This allows the CDM to decrypt the video and send it to your browser’s media player to stream the decrypted content.
A good DRM system should protect that decrypted data and only let you stream the content in your browser. But, Google’s system lets you copy it as it streams.
David Livshits from the Cyber Security Research Center at Ben-Gurion University in Israel and Alexandra Mikityuk with Telekom Innovation Laboratories in Berlin, Germany, alerted Google to the problem on May 24. But, Google is yet to release a patch.
The researchers created a proof-of-concept executable file that easily exploits the vulnerability, and produced a brief video to demonstrate it in action.
The researchers believe that Google can easily patch the flaw. But to fix the problem permanently Google might need to design the CDM so that it runs inside the browser’s Trusted Execution Environment or TEE. The TEE would act like a protective tunnel so that the decrypted content is written to a protected memory space. This prevents someone from hijacking the content as it is going to the player.
A Google spokesperson told Wired, that the company’s looking closely at the problem. Unfortunately, the issue is not restricted to Chrome. Browsers that use the Chromium source code are also vulnerable. Chromium is the open source version of the Google Chrome browser.
Chrome has long been an open-source project and developers have been able to create their own versions of the browser that, for example, may use a different CDM or include modified CDM rendering paths.
We do not know how much Google can do about it. There is no way to know if other browsers also have this problem. The researchers limited their research to the desktop version of Chrome.
Also, it is not certain that this is a Google-specific problem. Firefox and Opera also use Widevine, so it is possible that they might behave the same way. Safari uses Apple’s FairPlay CDM, and Microsoft’s Internet Explorer and Edge browsers use Microsoft’s PlayReady CDM. The researchers have not examined those CDMs yet.
While this may be a small problem, Google needs to do something to address this issue before Hollywood and other online streaming services lose their trust on their browser.