WhatsApp popularity means its user are targeted for malwares and phishing attacks. Recently security firm Comodo Labs has discovered a new malware / phishing attack targeted specifically at businesses and consumers who might use the application.
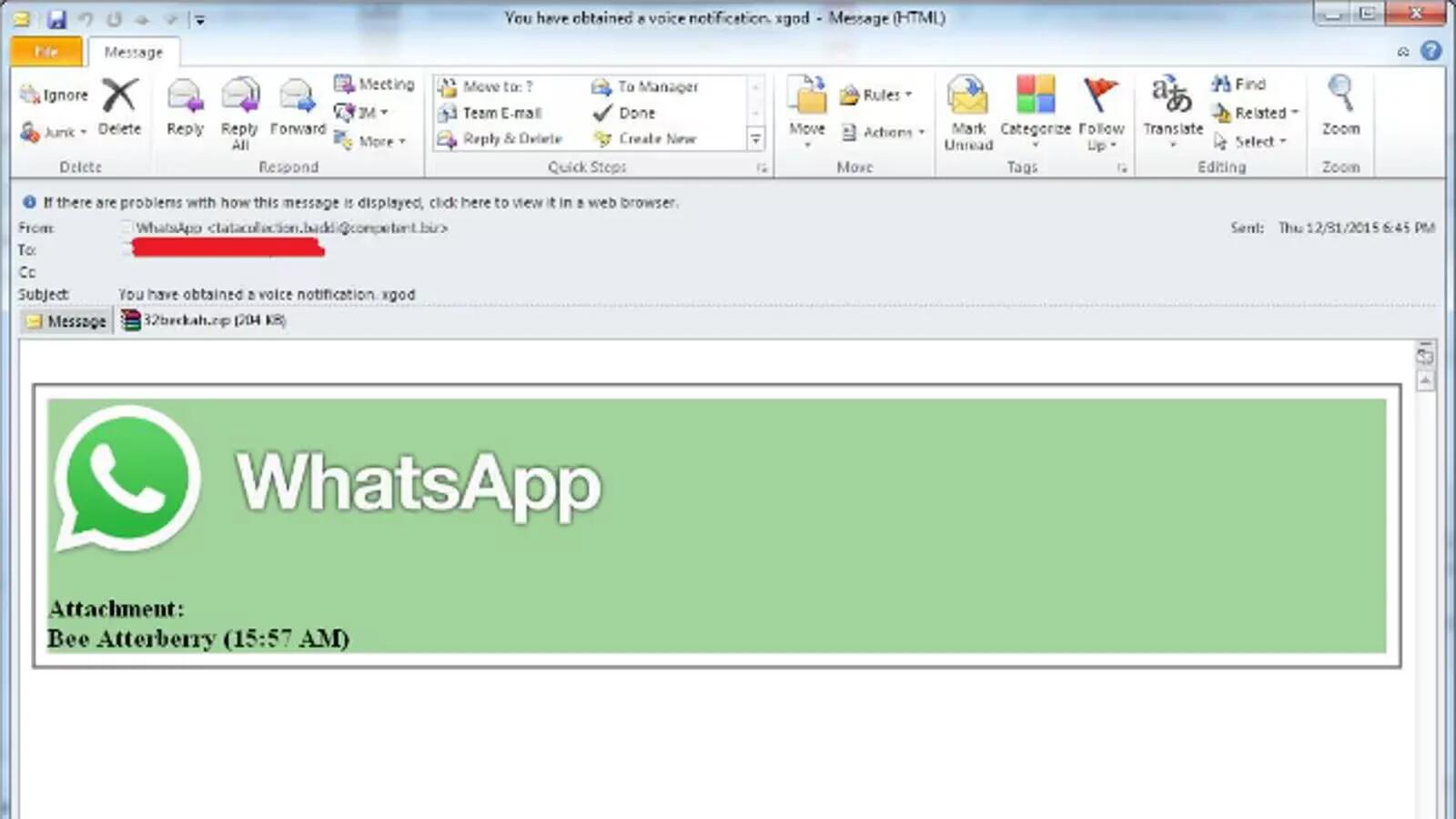
The phishing attack involves sending fake emails representing the information as official WhatsApp content to convince users to click on the link to spread malware.
The phishing emails are sent from a rogue email address, disguised with an umbrella branding “WhatsApp”, but if users look at the actual FROM email address, they will see it is not from the company. The emails also contains various convincing subjects like, “You have obtained a voice notification”, “An audio memo was missed”. The body of the email contains image and text to convince you the email is from WhatsApp.
If you receive emails from WhatsApp, keep in mind that WhatsApp is mobile based messaging service that only uses your phone number. They will never send notification mails to your email address. So it is advised to mark these emails as spam and delete them.
The second threat is discovered by a Indrajeet Bhuyan, which involved emoji’s to crash the WhatsApp application. According to Indrajeet,
In WhatsApp web, WhatsApp allows 65500-6600 characters.But after typing about 4200-4400 smiley browser starts to slow down. But since the limit is not yet reached so WhatsApp allows to go on inserting. so it crashes while we type and send and in mobile too when it receives it overflows the buffer and it crashes.
The exploit crashes the app on PC (Firefox and Chrome), and on Android (Marshmallow, Lollipop and KitKat), while on iPhone it just freezes the app a few seconds, rather than crashing it completely. A video showing the bug follows below.
If you receive this specially crafted message, then the only solution right now is to delete the whole conversation and start a fresh chat, because opening the message keeps on crashing WhatsApp unless the chat is deleted completely.
WhatsApp has promised a fix to this bug in their next update.
