According to a recent report, a database containing more than 267 million Facebook usernames and phone numbers have been exposed on the web without any password protection or any other authentication. By having the web URL anyone can access the database, as it does not require a password or any other authentication.
Security researcher Bob Diachenko partnered with Comparitech uncovered the Elasticsearch database, the database found to be open for nearly two weeks. The non-password-protected Elasticsearch cluster was located on December 14, but it was first indexed by search engines on December 4, 2019. The researcher notified the ISP that managed the IP address of the leaking server, and the database was taken down on December 19. However, this time we can say with certainty that malicious actors accessed it, as the data was posted on a darknet forum on December 12.
Security researcher Bob Diachenko discovered the unsecured database. The database is believed to be a “result of an illegal scraping operation or Facebook API abuse by criminals in Vietnam, according to the evidence”.
According to Comparitech, the database included a user’s Facebook ID, their phone number, full name, and a timestamp. The majority of the users affected were from the United States.
In total 267,140,436 Facebook users’ records were exposed. Most of the affected users were from the United States. The server included a landing page with a login dashboard and a welcome note.
Bob Diachenko
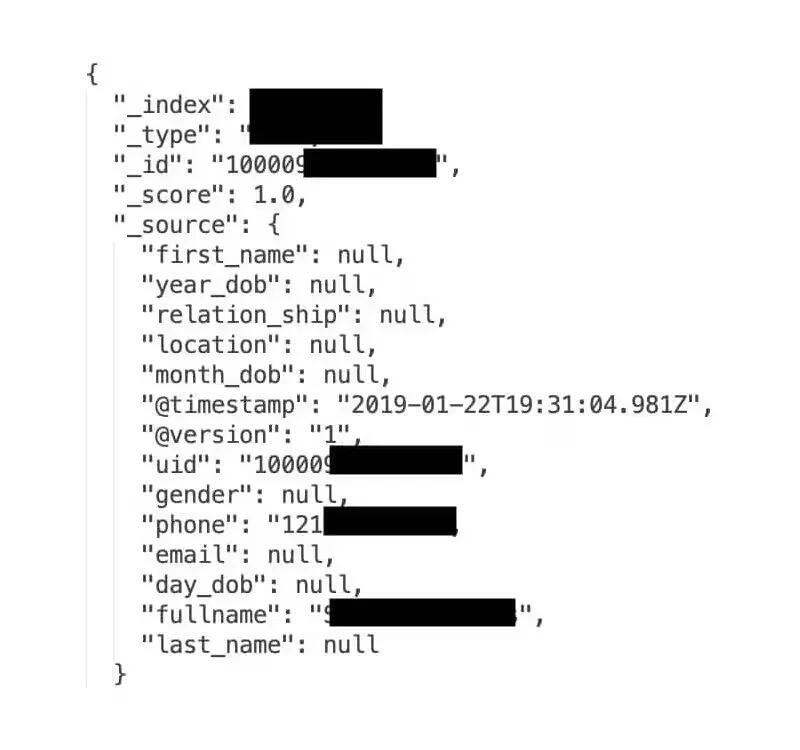
Facebook IDs are unique, public numbers associated with specific accounts, which can be used to discern an account’s username and other profile info. Though the database is no longer available online as of Thursday, it is possible that it was copied elsewhere prior to being taken down, Comparitech warned, noting that all the data appeared to be valid.
Facebook has not officially revealed the number of affected users. However, it is in the process of investigating the incident. A Facebook spokesperson speaking to AFP confirmed the database has been taken down and said: “We are looking into this issue, but believe this is likely information obtained before changes we made in the past few years to better protect people’s information”.
Facebook restricted the data in 2018, before that details such as check-ins, likes, photos, posts, videos, events, and groups, possibly the data scrapped before that.
It is unsure yet how the criminals obtained the data, but Comparitech says that “One possibility is that the data was stolen from Facebook’s developer API before the company restricted access to phone numbers in 2018”. Another possibility could be that “the data was stolen without using the Facebook API at all, and instead scraped from publicly visible profile pages”. Comparitech mentioned that having a user’s Facebook profile visibility set to “Public” makes it easier for criminals to scrape their data.
Knowing a person’s full name, Facebook profile, and phone number open up a whole host of abusive possibilities for hackers with malicious intent. Phishing campaigns are a common example of how to deploy this type of data.
Another way to take advantage of the available info is to launch large-scale SMS spamming campaigns. Remember, people are likely to click on a URL that they have received via SMS, so downloading a malware payload such as a banking Trojan, or visiting a well-crafted phishing page are the most prevalent dangers faced by the exposed individuals right now.
To prevent this scraping from happening again in the future,
- Open Facebook and go to Settings
- Click Privacy
- Set all relevant fields to Friends or Only me
- Set Do you want search engines outside of Facebook to link to your profile to No
It looks like Facebook users have no respite from data leaks. There have been multiple such incidents concerning the social media platform since the well-known Cambridge Analytica fiasco. The only real way to keep your personal information safe is to not put it out there on Facebook.
