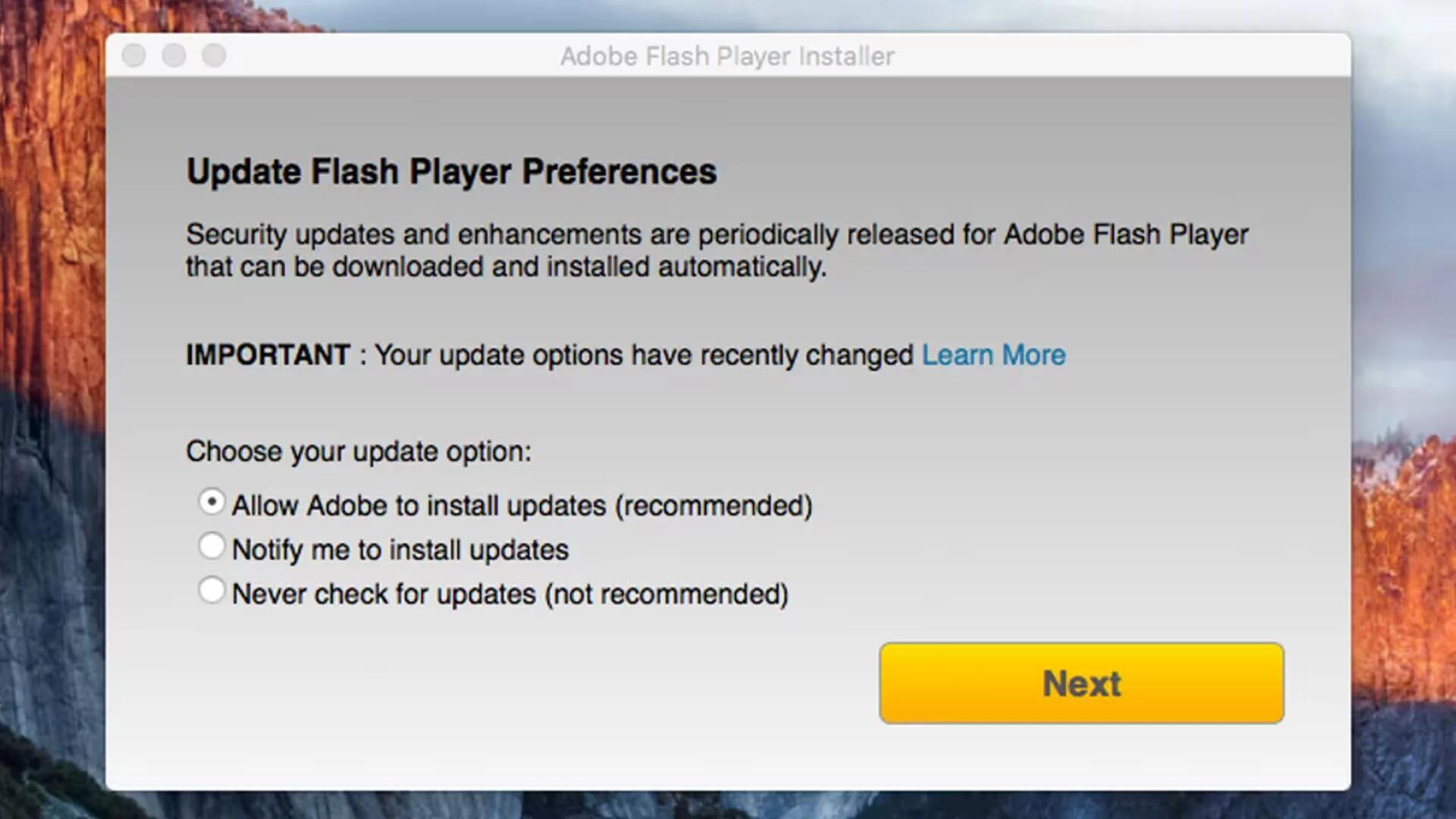
According to a report from MalwareBytes, A new piece of backdoor malware that was originally found on Windows has been ported to the Mac for the first time. Originally believed to be of Russian origin, the “Snake” malware was also known as “Turla” and “Uroburoshas” has been infecting Windows systems since 2008 and was ported to Linux systems in 2014 before making its way to the Mac. This highly sophisticated malware disguises itself as a legitimate Adobe Flash Player installer and burrows into pre-existing MacOS folders making it harder to spot.
The Snake malware was found earlier this week in an installer masquerading as Adobe Flash Player, buried inside a file named “Install Adobe Flash Player.app.zip.” It is designed to look like a legitimate Adobe Flash installer but is signed by an illegitimate but valid certificate. Having used a valid developer’s certificate, the malware was set to run free on macOS even with Gatekeeper enabled. These certificates were created to help validate applications with Gatekeeper but lately have been used to spread malicious software. This is the second reported malware incident in the past week using a valid certificate.
While the malware does, actually, install Adobe Flash Player, it is also accompanied by additional software that is malicious and designed to provide a backdoor into the Mac. The malicious files are well hidden in the /Library/Scripts/ folder and disguised as an Adobe launch process.
In all, this is one of the sneakier bits of Mac malware lately. Although it’s still “just a Trojan”, it’s a quite convincing one if distributed properly. Although Mac users tend to scoff at Trojans, believing them to be easy to avoid, this is not always the case.
The Snake malware version currently out in the wild contains debug code and its certificate was signed in February of this year. This leads Fox-IT to believe it may not have even been operational yet, but would soon be used on targets.
Luckily, if anyone does have the Adobe Flash Player.app.zip file on their system, macOS’ Gatekeeper will no longer show the developer certificate as valid. Apple already revoked the certificate that the Snake malware was using to infect Mac machines, but another iteration could pop up, so Mac users should be aware of the possibility.
Those infected by Snake malware are vulnerable to having data stolen, including login information, passwords, and unencrypted files.
To easily check if a system has been infected by the Snake backdoor malware, run a scan with Malwarebytes for Mac. The free software will detect Snake as OSX.Snake and remove it.
If you would like to manually check for infection, the backdoor malware installs the following various components:
/Library/Scripts/queue
/Library/Scripts/installdp
/Library/Scripts/installd.sh
/Library/LaunchDaemons/com.adobe.update.plist
/var/tmp/.ur-*
/tmp/.gdm-socket
/tmp/.gdm-selinux
Malwarebytes recommends changing passwords and contacting your business IT department if you were infected. The former is to secure yourself and online accounts, and the latter to mitigate any potential company damage.
To avoid malicious software, Apple recommends downloading content only from the Mac App Store or from trusted developers.
See Also: Google Improves Phishing Protection In Gmail For Android